Data Breach Detection
Our Data Breach Detection feature enhances your security by identifying leaked passwords before they lead to unauthorized access on your site. The feature actively scans for known leaked credentials and cross-references them with attempts to log in, sign up, or update a password. When a leaked password is detected, authentication is automatically suspended (if configured), preventing potential security risks.
You can enable the protection directly in your ReachFive Console to add protection around:
Users with leaked credentials
The users that our Data Breach Detection feature have identified as having leaked credentials will have the has_leaked_credentials boolean set to true on their user profile.
You can also filter to find these users directly in the ReachFive Console. When you search for users in the ReachFive Console based on this criteria, all users with leaked credentials are returned regardless of their suspension status.
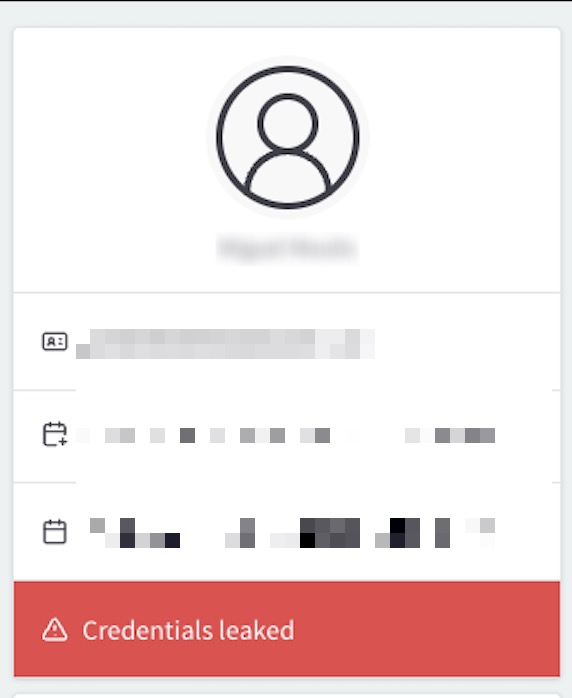
Users with leaked credentials also have a flag on their user profile card in the ReachFive Console.
Sign up
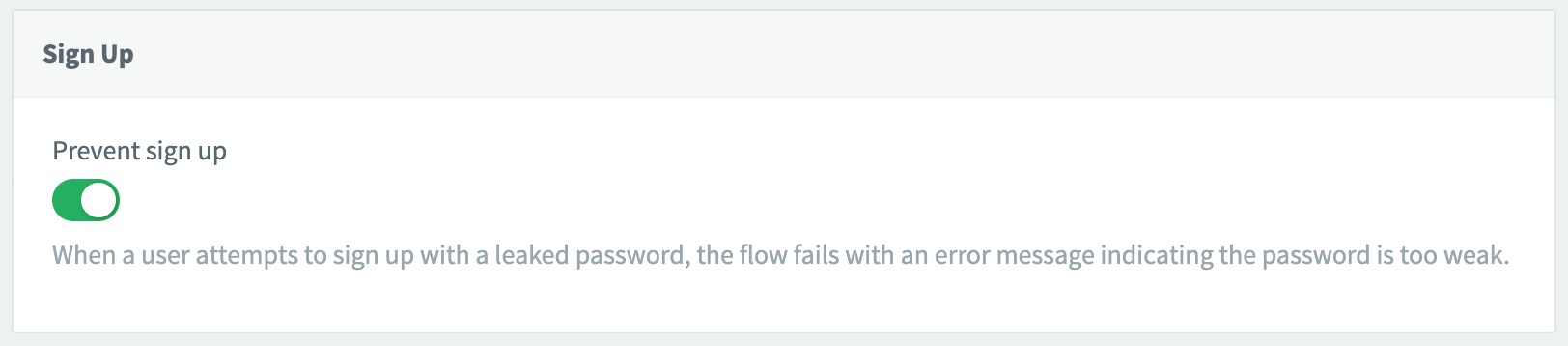
When a user attempts to sign up with a leaked password, the sign up flow fails, telling the user that his or her password is too weak. This ensures that no one can sign up with a known leaked password.
The API rejects the registration immediately so your UI can display whatever “password too weak” message matches your experience. No outbound notification is sent because the profile never finishes creation.
To enable data breach detection for sign up:
-
In your ReachFive Console, go to .
-
Under the Sign up section, toggle on the feature.
-
Don’t forget to Save your input.
Log in
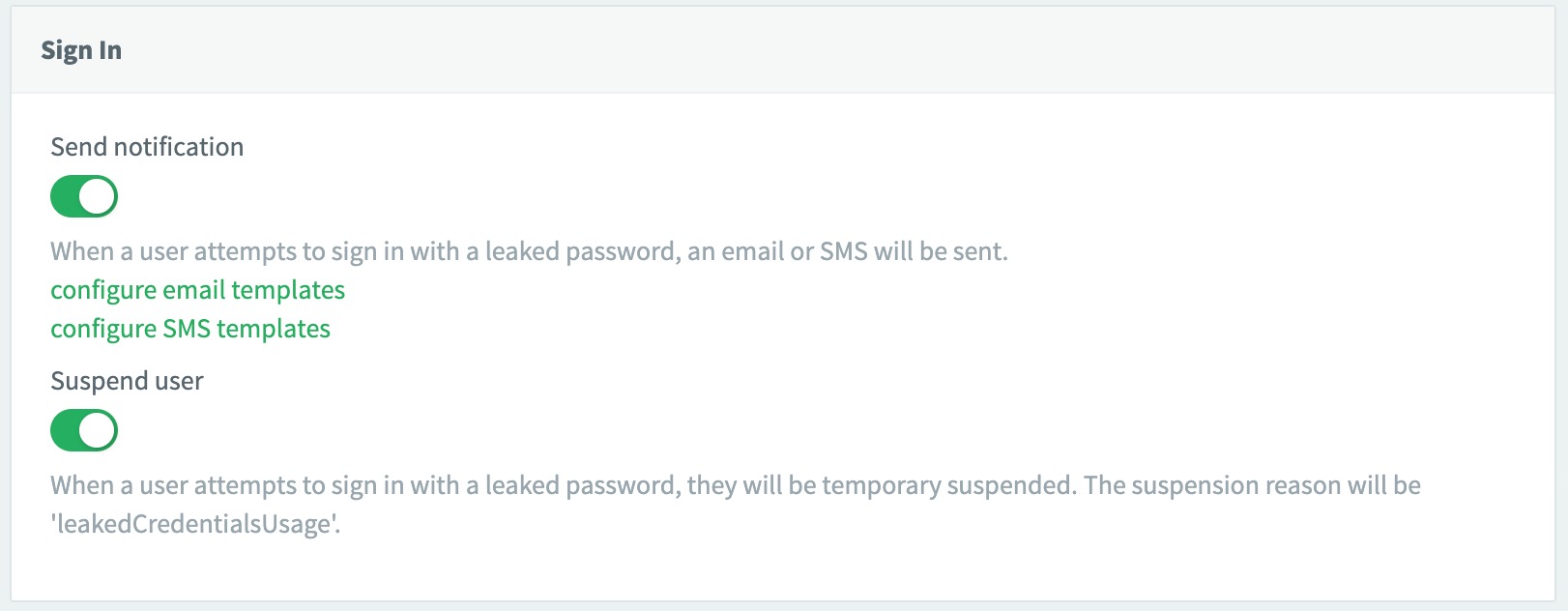
When a user attempts to log in with a leaked password, the user is sent an email or sms depending on what identifier the user attempted to log in with (if enabled).
You can also suspend the user with the suspension reason set to leakedCredentialsUsage.
The API returns an error immediately, so your UI can block the attempt and guide the user toward password reset or support without exposing whether the account exists. If notifications are enabled, we deliver the corresponding email or SMS template and, when the Suspend User toggle is on, we suspend the profile during the same login attempt so all subsequent calls fail until the password is reset or support clears the suspension.
| By default, the Suspend User toggle is disabled. In order to suspend users automatically when they attempt to log in with leaked credentials, you must manually enable this option. |
-
In your ReachFive Console, go to .
-
Under the Log in section, toggle on the feature. For Log in, you can choose to notify the user and/or suspend the user.
-
Don’t forget to Save your input.
Leaked Credentials Notification
Sent to user when they attempt to sign in with leaked credentials
This template should be used to notify users that they attempted to sign in with leaked credentials.
-
Enable the template.
-
Enter the sender’s email in the From field.
-
Write your Subject.
Credentials leaked -
Write your Message for the template.
<p>Hello {{user.given_name}},</p> <p>Your credentials have been identified in a potential data breach. Please consider resetting your password and enabling MFA. Be sure to monitor your account activity.</p> -
Don’t forget to Save your input.
Leaked Credentials Notification
Sent to user when they attempt to sign in with leaked credentials
This template should be used to notify users that they attempted to sign in with leaked credentials.
-
Go to on your ReachFive Console.
-
Toggle to the Leaked Credentials Notification tab.
-
Enable the template by ticking the Enabled checkbox.
-
Use the Message section to write your customised template like the example below:
Hi {{user.given_name}}. Your credentials have been identified in a potential data breach. Please consider resetting your password and enabling MFA. Be sure to monitor your account activity. -
Don’t forget to Save your input.
Password update
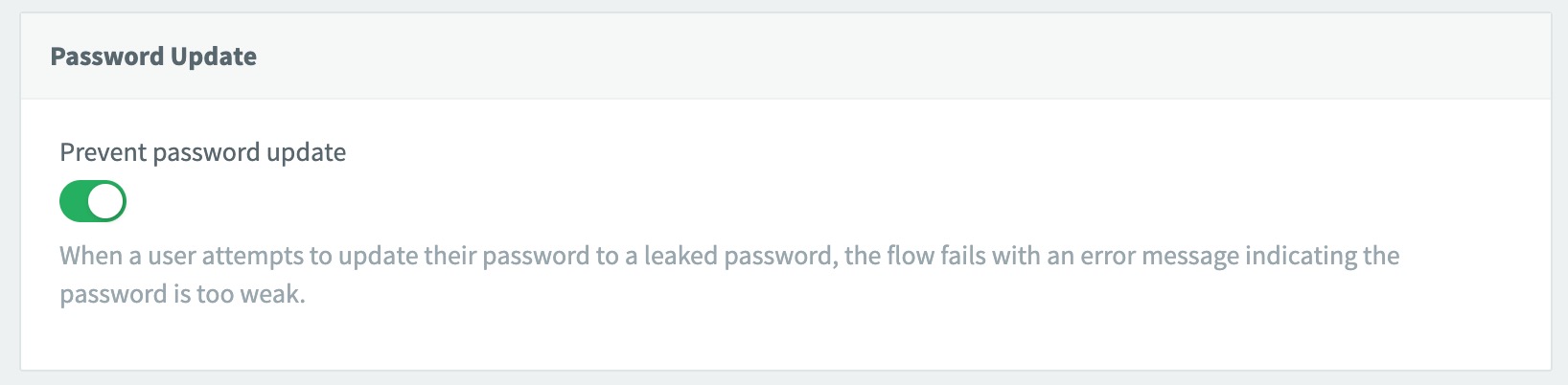
When a user attempts to update or reset his or her password to a known leaked password, the flow fails with an error, telling the user that his or her password is too weak. This ensures that no one can update their password with a leaked password.
The password change call returns the leaked credentials error while keeping the user signed in, giving your UI space to prompt for a stronger password without forcing a new login.
-
In your ReachFive Console, go to .
-
Under the Password Update section, toggle on the feature.
-
Don’t forget to Save your input.
Scanning job
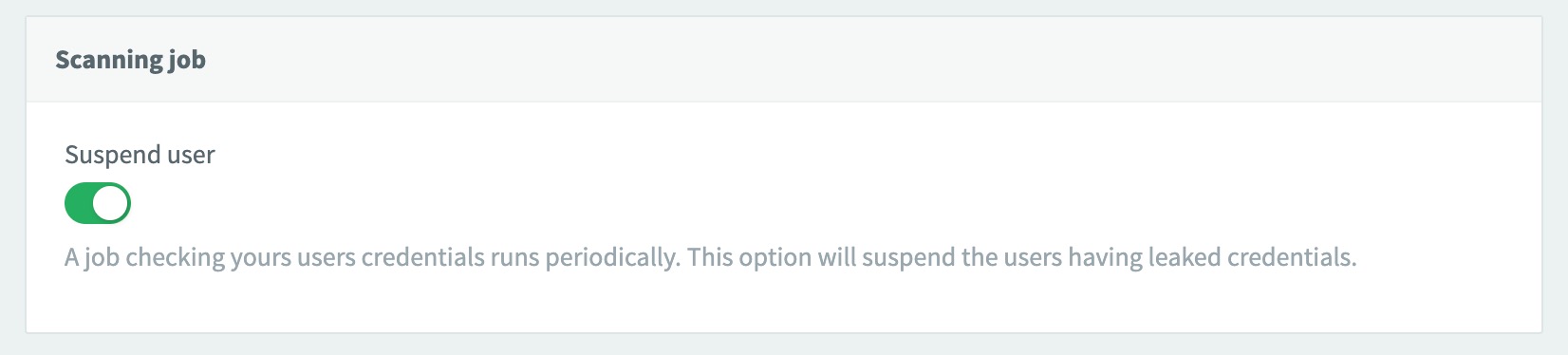
To run a job that automatically suspends any users found in the Data Breach Detection database.
| By default, the Suspend User toggle is disabled. In order to suspend users automatically when they are found in the Data Breach Detection database, you must manually enable this option. |
-
In your ReachFive Console, go to .
-
Under the Scanning job section, toggle on the feature.
-
Don’t forget to Save your input.
Hide suspension reason
To hide the suspension reason in the API response:
-
In your ReachFive Console, go to .
-
Under the Suspension reason section, toggle on the feature.
-
Don’t forget to Save your input.
| Our templates cover the outbound notifications, while your on-screen copy explains next steps (e.g., password reset, contacting support) using the error codes we return. |