Rate limiting
Rate limiting controls the number of incoming and outgoing requests to or from a network. For example, let’s imagine you are using a particular service’s API that is configured to allow 100 requests/minute. If the number of requests you make exceeds that limit, an error is triggered.
ReachFive APIs employ safeguards against bursts of incoming traffic for each tenant to help maximize its stability. The Rate Limiter setting in the ReachFive Console allows you to change the maximum number of calls from the same IP within a defined timeframe.
When an IP reaches the limit, the server responds with 429 Too Many Requests.
Rate limiting endpoints
By default, all endpoints below allow 20 requests every 60 seconds from the same IP.
| Each endpoint specifies whether you can configure the maximum number of attempts and sliding window duration. |
| Operation | Endpoint | Configurable |
|---|---|---|
Retrieve access token |
||
Retrieve password strength |
||
Revoke refresh token |
||
Login with password |
||
Sign up new user |
||
Sign up new user and return token |
||
Request password reset |
||
Update password |
||
Update phone number |
||
Verify phone number |
||
Update email |
||
Verify email |
||
Start passwordless flow |
||
Verify passwordless |
||
Verify SMS auth code |
Configure rate limits
Some ReachFive API endpoints have configurable rate limits. You can configure these from your ReachFive Console.
Prerequisites
-
You must have access to the ReachFive Console.
-
You must have a Developer, Manager, or Administrator role.
Instructions
-
Go to .
-
Go to your desired configurable endpoint.
-
Set the Maximum number of attempts by entering in the value or using the up and down arrows.
-
Set the Sliding window duration by entering in the value or using the up and down arrows.
This is specified in seconds.
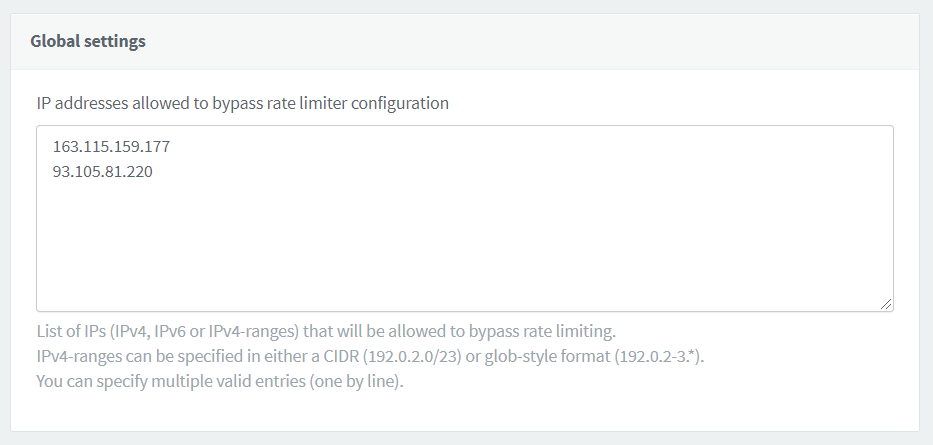
Bypass rate limit configuration
If you want, you can add IP addresses to a whitelist under Global settings. The IP addresses listed here are not subject to any rate limit from any ReachFive endpoint.
-
Go to .
-
Under Global settings, list one URL per line.
-
Don’t forget to Save your input.
IPv4 addresses
We support both standard IPv4 address format as well as IPv4 address ranges.
The syntax supports ranges of IPv4, as you can see in the following examples:
-
Using
/z, the CIDR notation, you can define a range of usable addresses throughout the 4 octets:10.0.0.0/24will accept addresses from10.0.0.0to10.0.0.255 -
Using
*.*, called asterisk octet, you can wildcard a whole octet of addresses:10.0.0.*.*will accept addresses from10.0.0.0to10.0.0.255 -
Using
x-y, called hyphenated octet, you can define a specific range of allowed addresses:10.0.0.15-25will accept addresses from10.0.0.15to10.0.0.25 -
You can mix both asterisks and hyphenated patterns, as long as you respect rules below:
10.0.1-10.*will accept addresses from10.0.1.0to10.0.10.255
|
There are specific rules to follow when using this syntax:
|
Enable True Client IP key
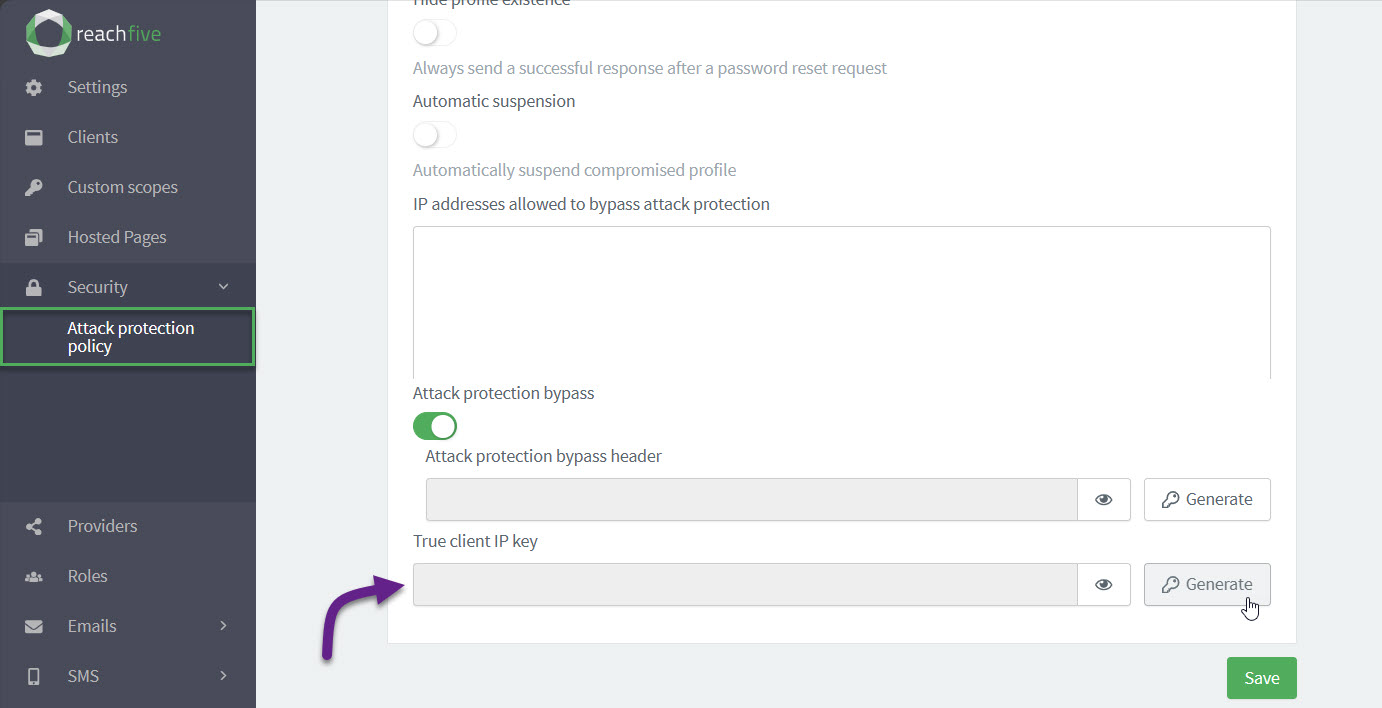
If you want your backend requests to be protected thanks to our security modules, you must enable the option from your ReachFive Console. The True Client IP Key is the key enabled and generated automatically in the ReachFive Console.
Any request coming from a backend that has True-Client-IP in the header must contain a True-Client-IP-Key header along with it.
This True-Client-IP-Key in the header must match the True Client IP Key you enabled and generated in the ReachFive Console.
The True-Client-IP header must contain the IP of the end user.
This IP will be present in the user events generated by the request.
| Requests that do not contain the matching secret are not accepted. |
To enable the option:
-
Go to .
-
Under True client IP key, click Generate.
-
In the dialog, confirm you want to Generate a new secret header.
-
-
Under True client IP key, you can now view and copy the key.