Authorization code grant with PKCE
Recommended
The Authorization Code Flow with PKCE accepts a secret that is created by the application and is verified by the authorization server.
This is known as the Code Verifier, and it’s used to create the Code Challenge which is sent over HTTPS to retrieve the authorization code.
| For more in-depth implementation details, check out Authentication (Single-page application). |
Flow
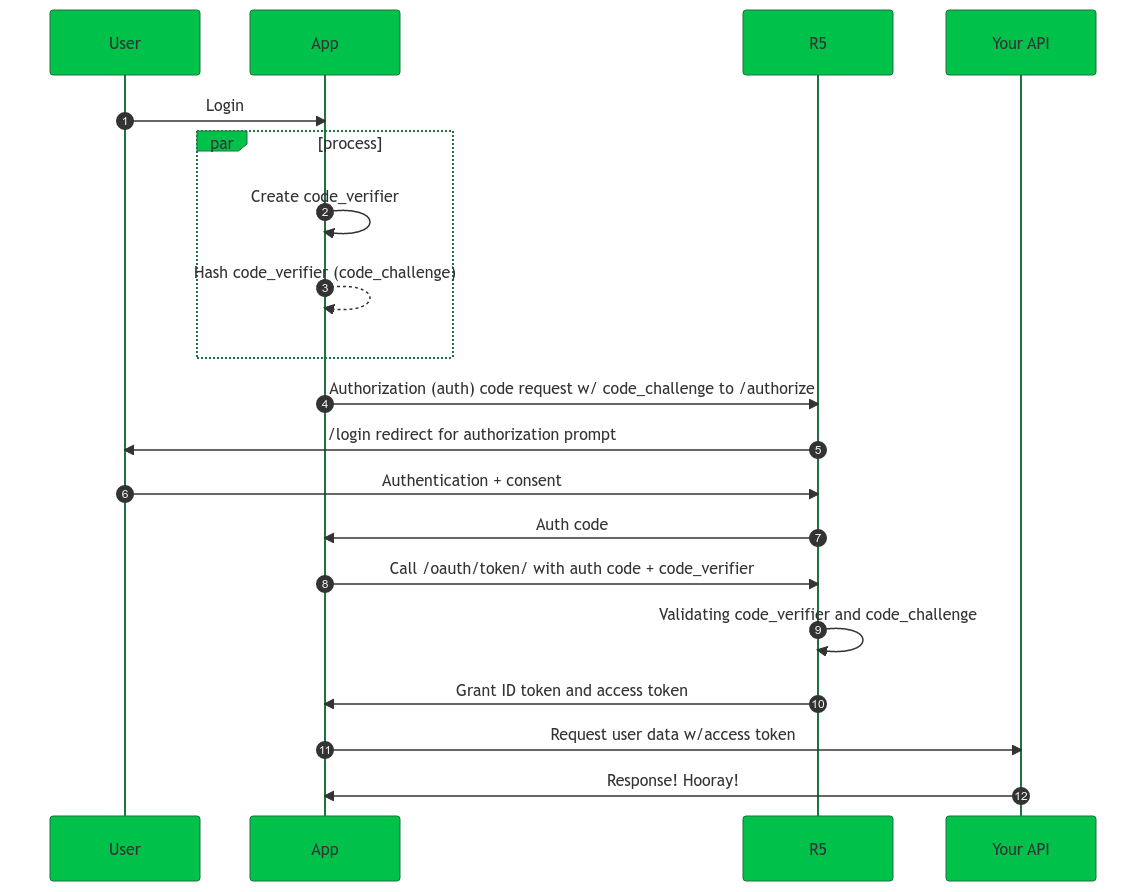
-
A user logs in from your app.
-
Calling application generates the
code_verifier -
Calling application hashes the
code_verifierto create thecode_challenge. -
ReachFive’s SDK redirects the user to the ReachFive Authorization Server
/oauth/authorizeendpoint with thecode_challenge. -
ReachFive’s Authorization Server redirects the user to the login and auth prompt.
-
The user authenticates through one of the login options.
Users may see a consent page listing the permissions ReachFive will give to the regular web application. -
ReachFive’s Authorization Server stores the
code_challengeand redirects the user back to the application with an authorization code.This is for one-time use only. -
ReachFive’s SDK sends the code as well as the
code_verifierto the ReachFive Authorization Server/oauth/tokenendpoint. -
ReachFive’s Authorization Server verifies the
code_challengeandcode_verifier. -
ReachFive’s Authorization Server responds with an ID Token and Access Token.
This could also be a refresh token. -
Your app can then use the Access Token to call the API to access information about the user.
-
Your API responds with the requested data.
PKCE importance
The PKCE flow is relevant even for server-side integrations where the client_secret is used. Because servers are often stateless, when a server-side app receives an authorization code, it exchanges it at /oauth/token. Using PKCE in server-side apps ensures that only legitimate clients are able to exchange the code.
PKCE flow with confidential clients
It’s important to understand how PKCE interacts with different types of clients and application architectures. While PKCE is essential for public clients like SPAs and mobile apps, its role with confidential clients (such as traditional server-side applications) can be less obvious. Let’s clarify how PKCE works in these scenarios and what you need to consider when integrating it with your application’s authentication flow.
Enforcing PKCE on confidential clients
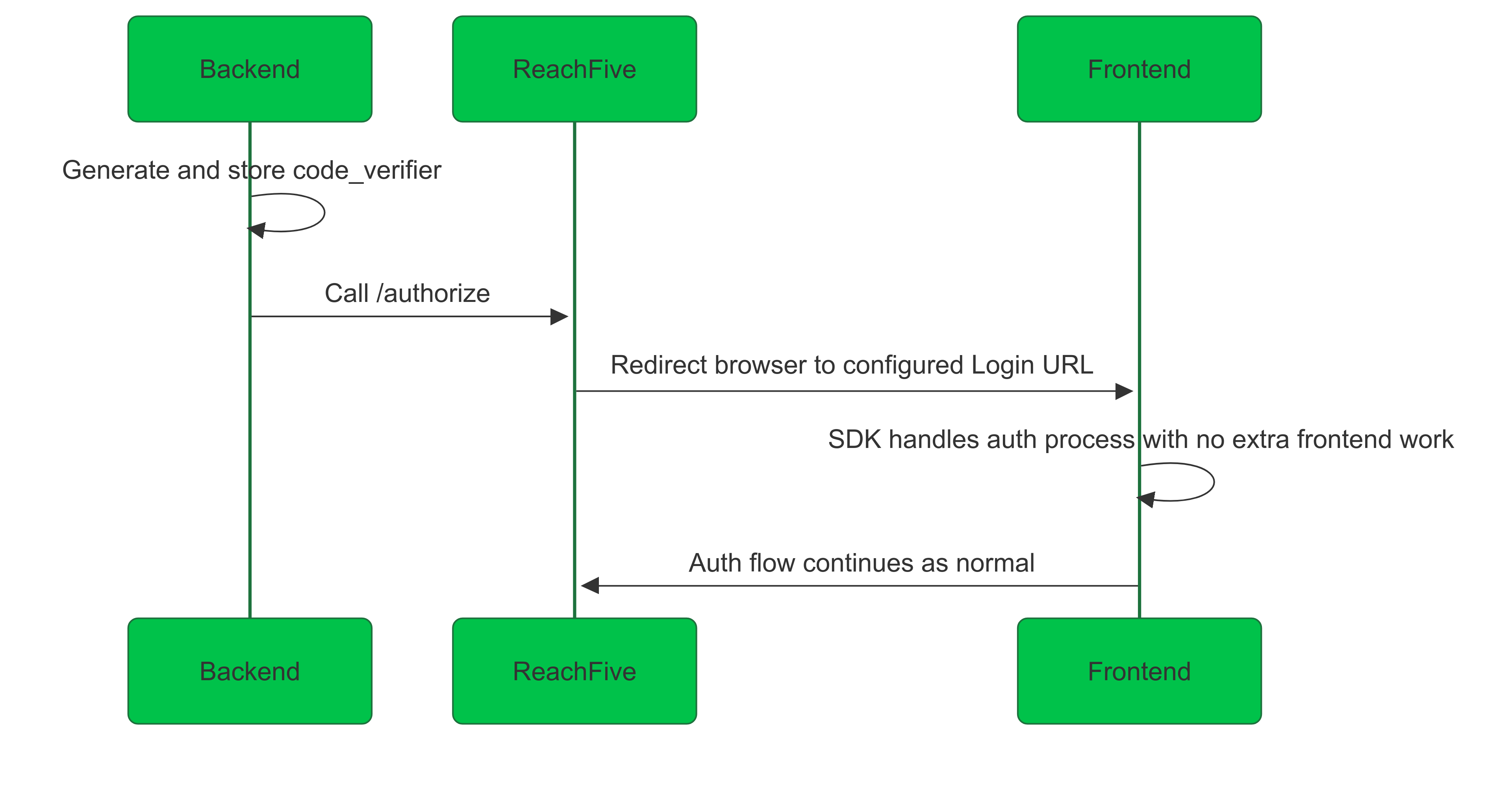
Even if you enforce PKCE for a client, if the client is confidential (uses a client secret, e.g., with "Post" or "Basic" authentication), the SDK will not generate the code_challenge on the frontend.
This is because the secure part of the flow (the code exchange) must always be handled by the backend.
The only way to use PKCE with the SDK for confidential clients with ReachFive is to enable the orchestration option.
In this setup:
-
The backend initiates the flow, generates and stores the
code_verifier, and calls/authorize. -
ReachFive redirects the browser to the configured Login URL.
-
The SDK on the frontend automatically detects the orchestration token; no additional work is needed on the frontend.
-
The authorization server (ReachFive) then handles the code exchange, using the stored
code_verifierto create thecode_challengeand complete the flow.
This orchestration approach ensures your OAuth/OIDC flow is compliant: every flow starts with /authorize, and the backend manages the sensitive parts.