Release notes
The release notes describe new features, enhancements, and fixes for the ReachFive platform. The latest release notes are found below. For previous releases, check out the sidebar.
For upcoming changes that require your attention, see the Attention page.
Other releases
The following shows other ReachFive releases for your convenience.
| SDK repository | Latest version | Docs |
|---|---|---|
MavenCentral |
||
SFCC Cartridge |
26 February 2026 (v2.152)
Production ✅
ReachFive v2.152 brings a few new features:
As always, we made some general improvements for you.
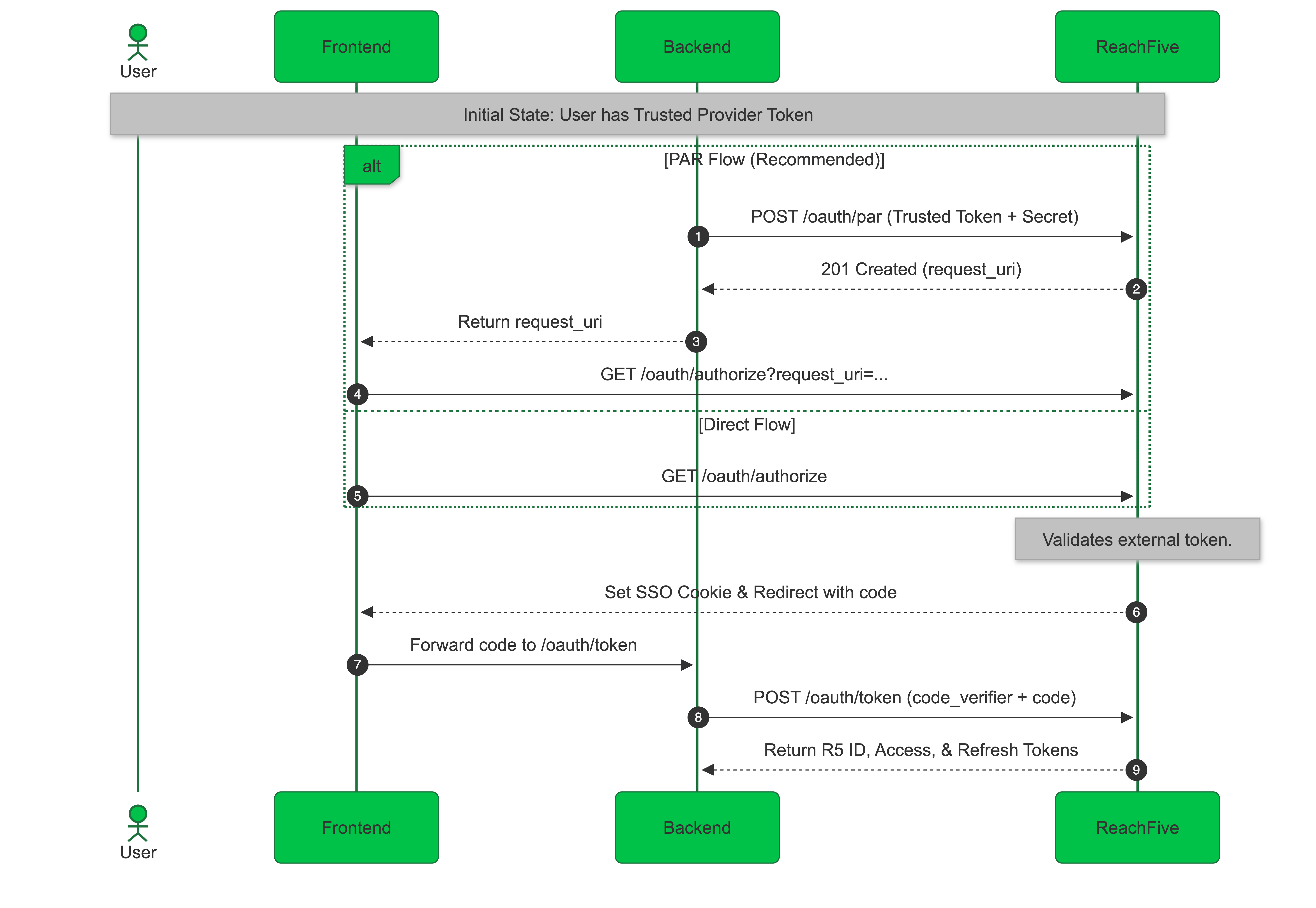
Pushed Authorization Request (PAR) endpoint
We have added the Pushed Authorization Request (PAR) /oauth/par endpoint, which lets clients push the authorization request parameters directly to the authorization server, improving security and efficiency in the authorization process.
Key advantages
-
Prevents sensitive parameters from being exposed in query strings.
-
Eliminates issues caused by excessively long URLs (especially when using PKCE).
-
Allows a backend to prepare and validate the authorization request before redirecting the user.
-
Improves security and integrity of the authorization flow.
How it works
-
The client sends a
POSTrequest to/oauth/parendpointBecause this is a direct server-to-server call, confidential clients must authenticate (e.g., by including their client_secret). -
The server validates and stores the request.
-
The server returns
request_uri -
The client then redirects the user to
/oauth/authorizewith therequest_urias a query parameter./oauth/authorize?client_id=<CLIENT_ID>&request_uri=<REQUEST_URI>...
For more details, see the /oauth/par endpoint.
Start token exchange flow from the frontend
You can now start the token exchange flow directly from the frontend by calling /oauth/authorize with the query parameter provider=custom_provider:<variant>.
You must ensure that the Allow token exchange from trusted external provider setting is enabled for your desired First-party Identity client in the ReachFive Console.
This flow is ideal for public clients, such as single-page applications (SPAs), that cannot securely store a client_secret.
By initiating the token exchange from the frontend, you can directly interact with the authorization server without needing an intermediate backend step, while still maintaining security best practices.
For more details on how to implement this flow, see Set up a client and Trusted providers respectively.
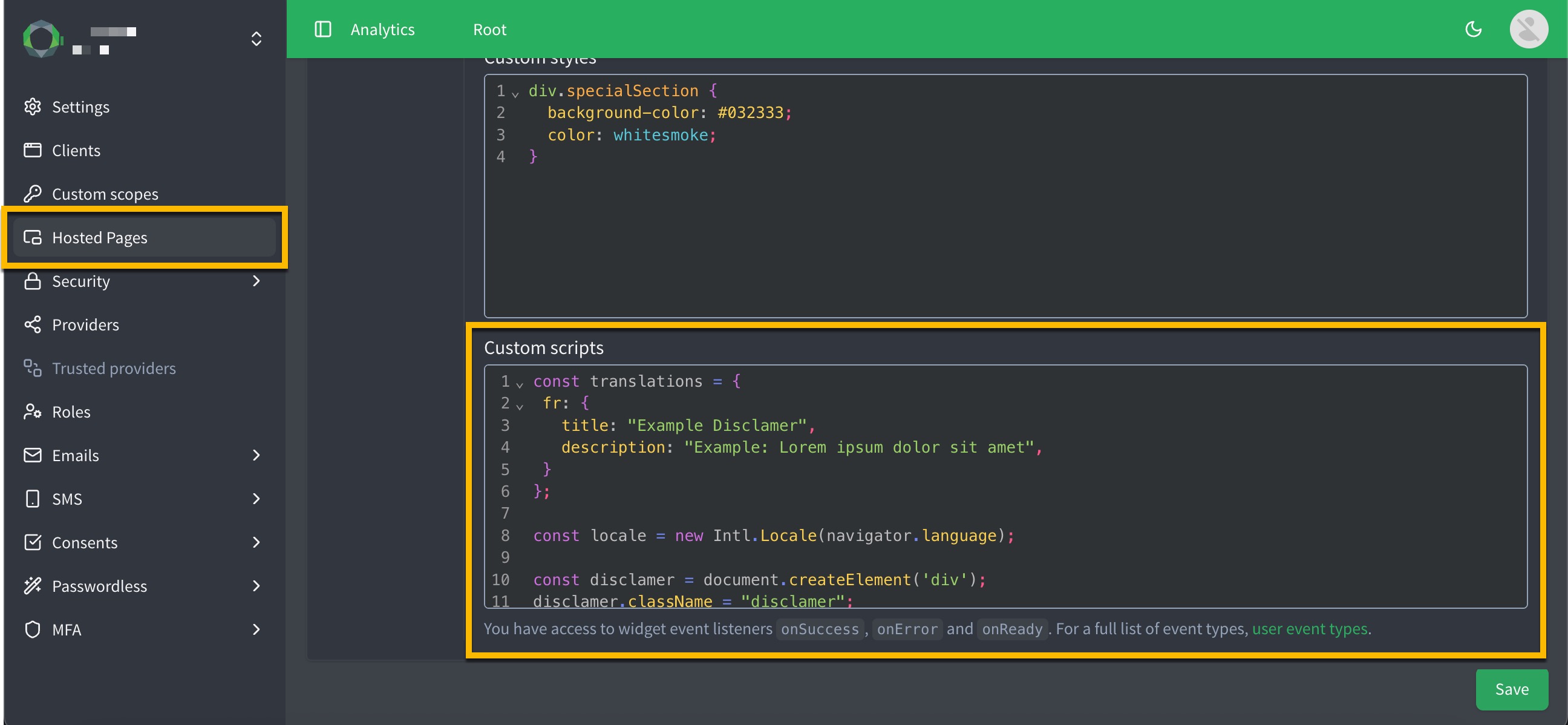
Use JavaScript directly in Hosted Pages
You can now use JavaScript directly in your Hosted Pages, allowing you to create more dynamic and interactive user experiences. This includes the ability to add custom scripts for enhanced functionality, such as form validation, dynamic content updates, and integration with third-party services.
Leverage available callback events to trigger your JavaScript code at specific points in the user journey.
The available events are OnError, OnReady, and OnSuccess, which provide flexibility in how and when your scripts are executed.
For more details, see Hosted Pages: Custom scripts.
To add custom JavaScript to your Hosted Page:
-
Go to your desired Hosted Page in the ReachFive Console at .
-
Scroll to Custom scripts on the page configuration screen.
-
Enter your JavaScript code in the Custom scripts area.
-
Don’t forget to Save your input.
Account Synchronization updates
With this release, we made several improvements to our Account Synchronization feature. This includes:
Expanded user event information for account synchronization events
We have expanded the depth of information provided for the account synchronization events:
-
account_synchronization_error -
account_synchronization_conflict
We did this to provide more context for these events, which help you troubleshoot and resolve synchronization issues more effectively. The additional information provides the specific conflict or synchronization error encountered during the account synchronization process as well as source and target user IDs for easier identification.
Possible errors:
-
error.profile.identifiersNotVerified -
error.profile.timestampOutdated -
error.emailOrPhoneNumber.required -
error.email.required -
error.profile.tooManyMatching
For more on this topic, see Account Synchronization events.
{
"date": "2026-10-07T09:54:34.183123Z",
"synchronization_id": "660e8400-e29b-41d4-a716-446655440000",
"source_user_id": "550e8400-e29b-41d4-a716-446655440000",
"type": "account_synchronization_error",
"failed_sync_error": "error.profile.identifiersNotVerified",
"failed_sync_message": "Can't synchronize because the identifier of the `target` profile isn't verified", (1)
"target_user_id": ["250e8401-e29c-41d3-a726-146655440001"]
}| 1 | <target> is used in this example, but it can be caused by either the target or source not being verified. |
{
"date": "2026-10-07T09:54:34.183123Z",
"synchronization_id": "660e8400-e29b-41d4-a716-446655440000",
"source_user_id": "550e8400-e29b-41d4-a716-446655440000",
"type": "account_synchronization_conflict",
"failed_sync_error": "error.Profile.timestampOutdated",
"failed_sync_message": "Can't synchronize because the target profile has already updated since synchronization attempt",
"target_user_id": ["250e8401-e29c-41d3-a726-146655440001"]
}Account Synchronization mapping improvements
For Account Synchronization, we now only consider consent types for mapping to be accepted or rejected, meaning as long as the type (such as opt-in or opt-out) match, the consent mapping is accepted.
Additionally, for custom fields with the SELECT type, we ensure only keys are needed to map between accounts.
General improvements
-
In the case of confidential clients, we have disabled reCAPTCHA verification for the
signup-tokenendpoint, allowing a more streamlined integration during while maintaining security.



