25 September 2025 (v2.143)
ReachFive v2.143 brings several new features:
-
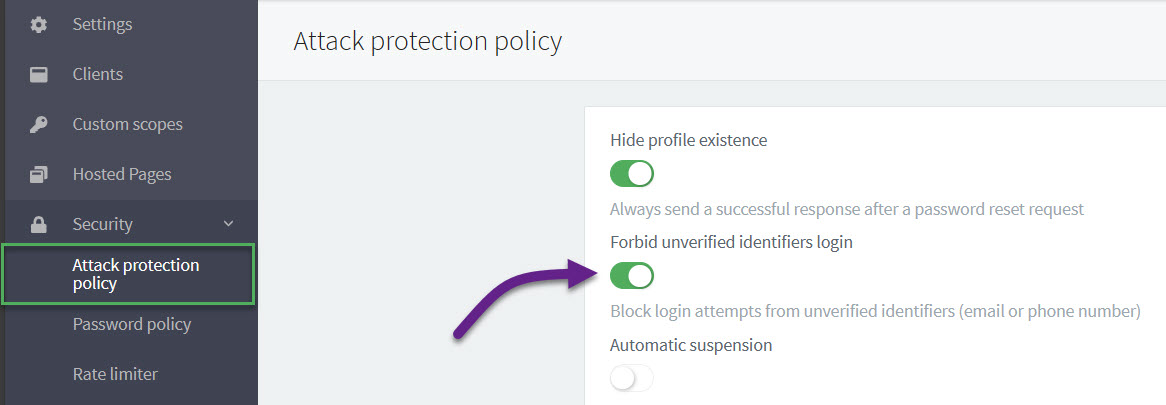
Now, you can prevent unverified users logging in at signup.
-
You can also track password reset request origins.
-
Additionally, you can now use Pub/Sub hooks for import events.
And as always, we fixed a few items for you.
Track password reset request origins
You can now track the origin of users when they request a password reset. This makes it easier to audit reset activity, monitor for suspicious behavior, and analyze trends across different applications or regions.
For more information on this subject, see Track user origins.
The /identity/v1/forgot-password endpoint now accepts an origin field.
This value is stored in the user’s origins[] array and included in the password_reset_requested event.
Supports passing an origin parameter with requestPasswordReset.
The showAuth widget automatically forwards the configured origin when triggering a password reset.
Use Pub/Sub hooks for import events
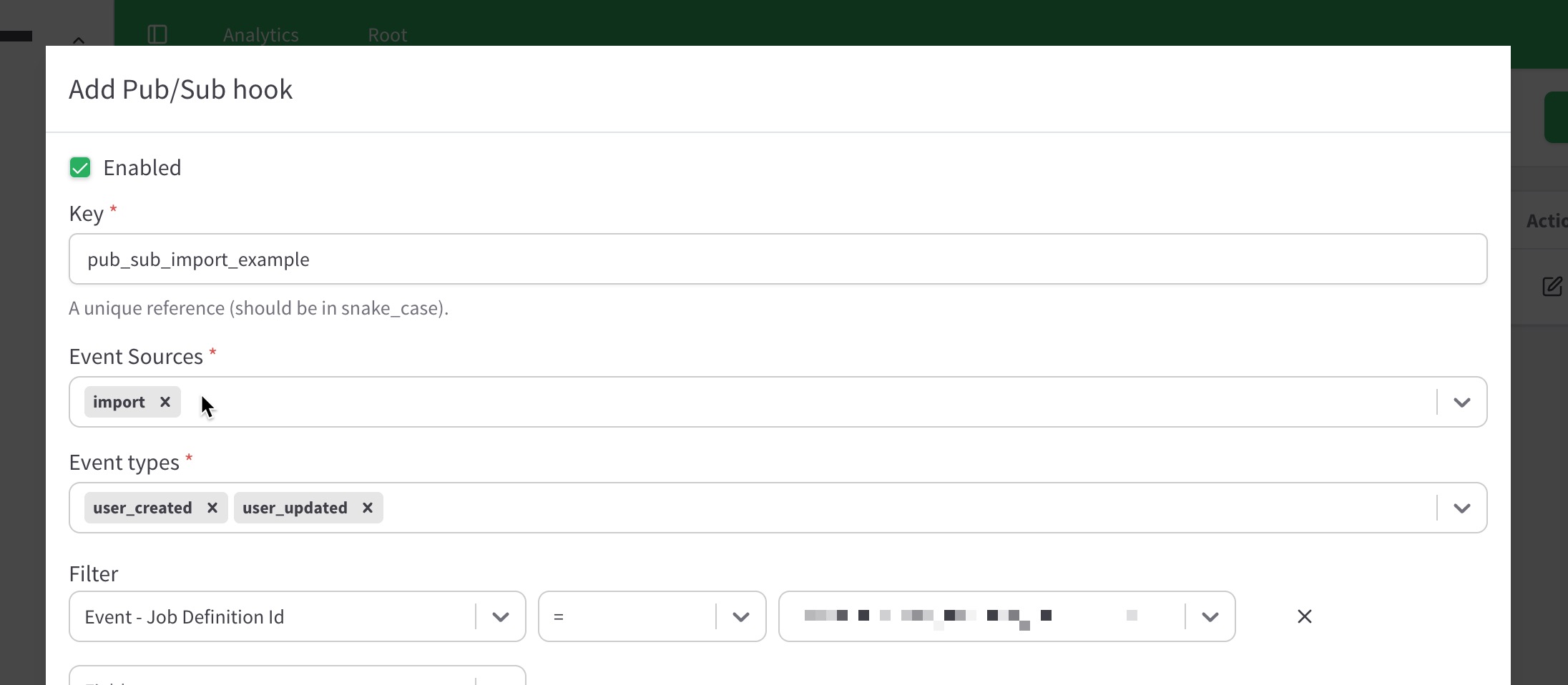
You can now use Pub/Sub hooks to receive events related to user import jobs.
-
Import job events on hooks
Import jobs with user events (e.g.,
user_created,user_deleted,user_updated,managed_user_created) are now published through Pub/Sub hooks. -
Event Source configuration
A new configuration option in the ReachFive Console allows you to include or exclude import job events, preventing existing hooks from receiving unexpected messages. When you choose
apiorimport, only relevant events for that event source is filterable, allowing only relevant information for you. -
Job definition tracking
You can now filter events by job definition ID directly in the ReachFive Console to reduce noise when running multiple jobs.
For full details, see Pub/Sub hooks.
Fixes
| Item | Fixed |
|---|---|
The trusted device authentication cookie had a fixed expiration period, which did not align with the configurable trusted device lifetime set in the ReachFive Console. |
✓ |