8 June 2023 (v2.94)
ReachFive v2.94 introduces the Attack protection bypass header, improves your control with managing compromised profiles, and adds some general improvements. We also fixed a few issues.
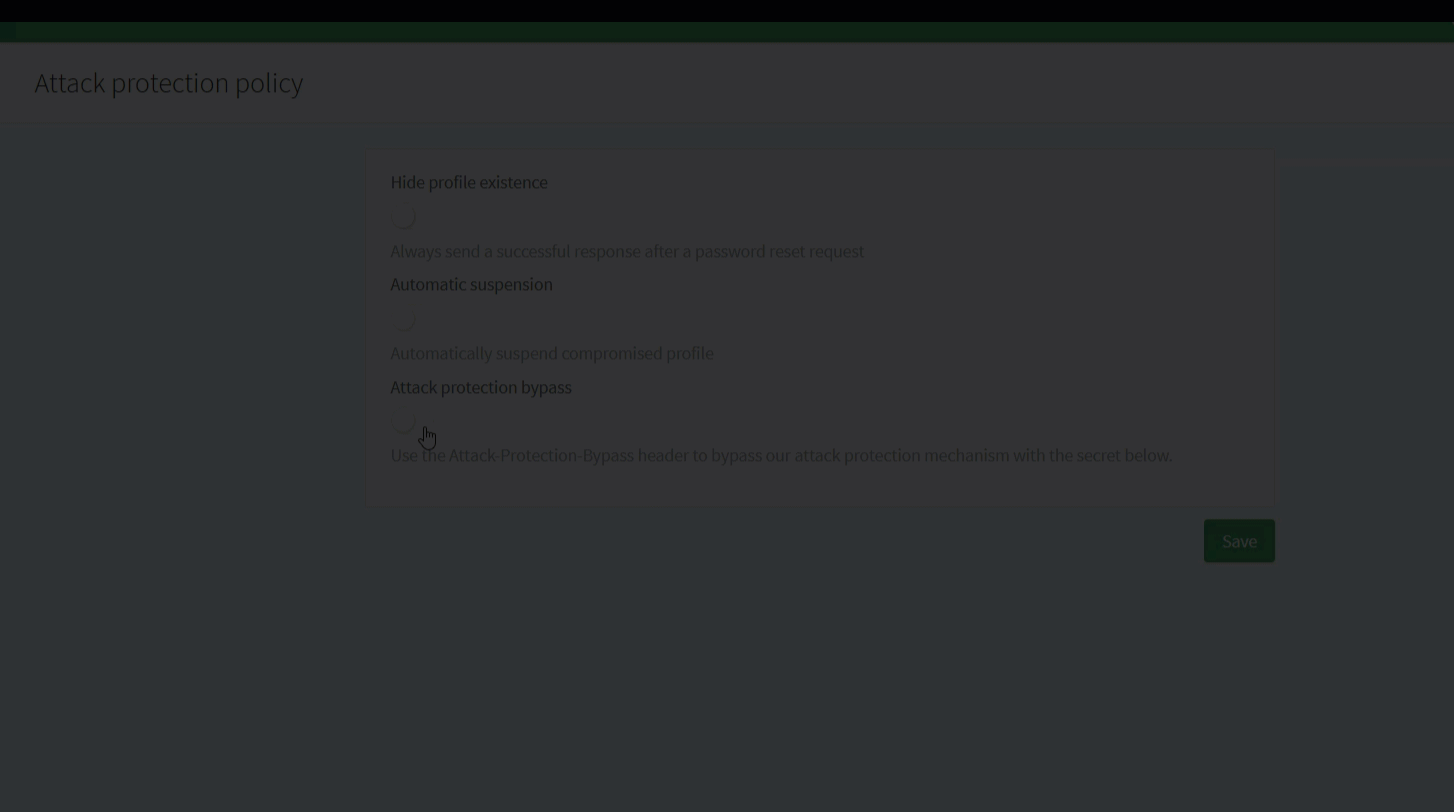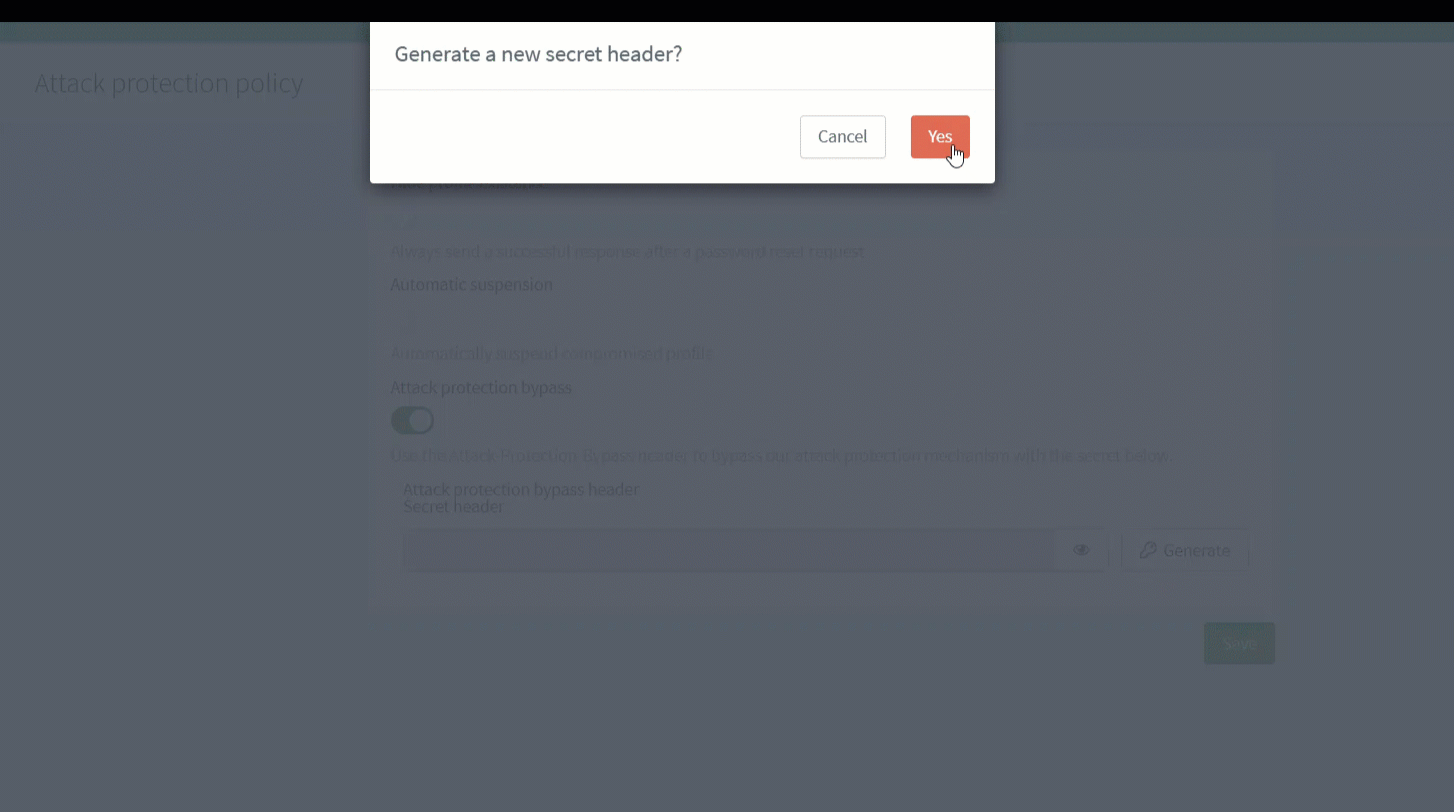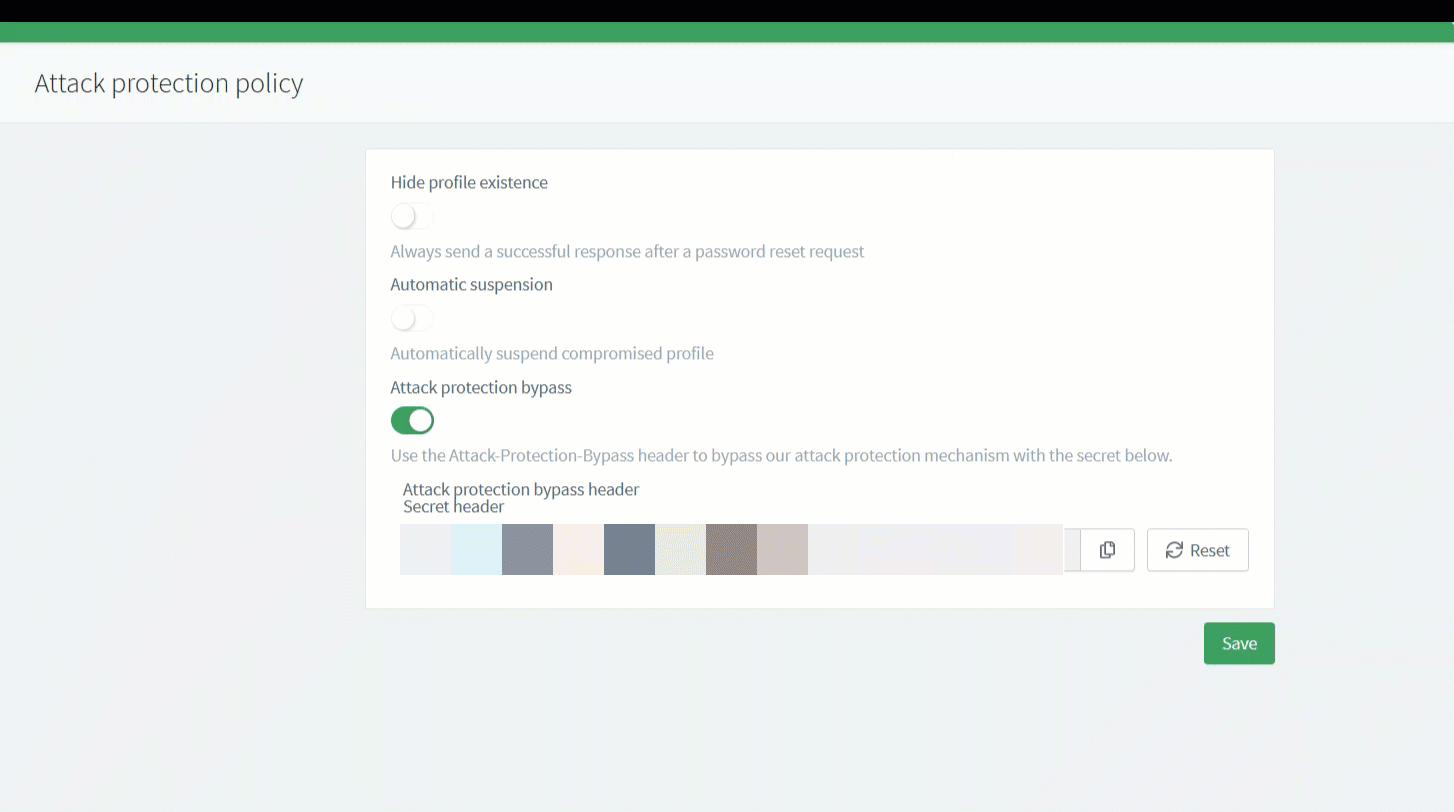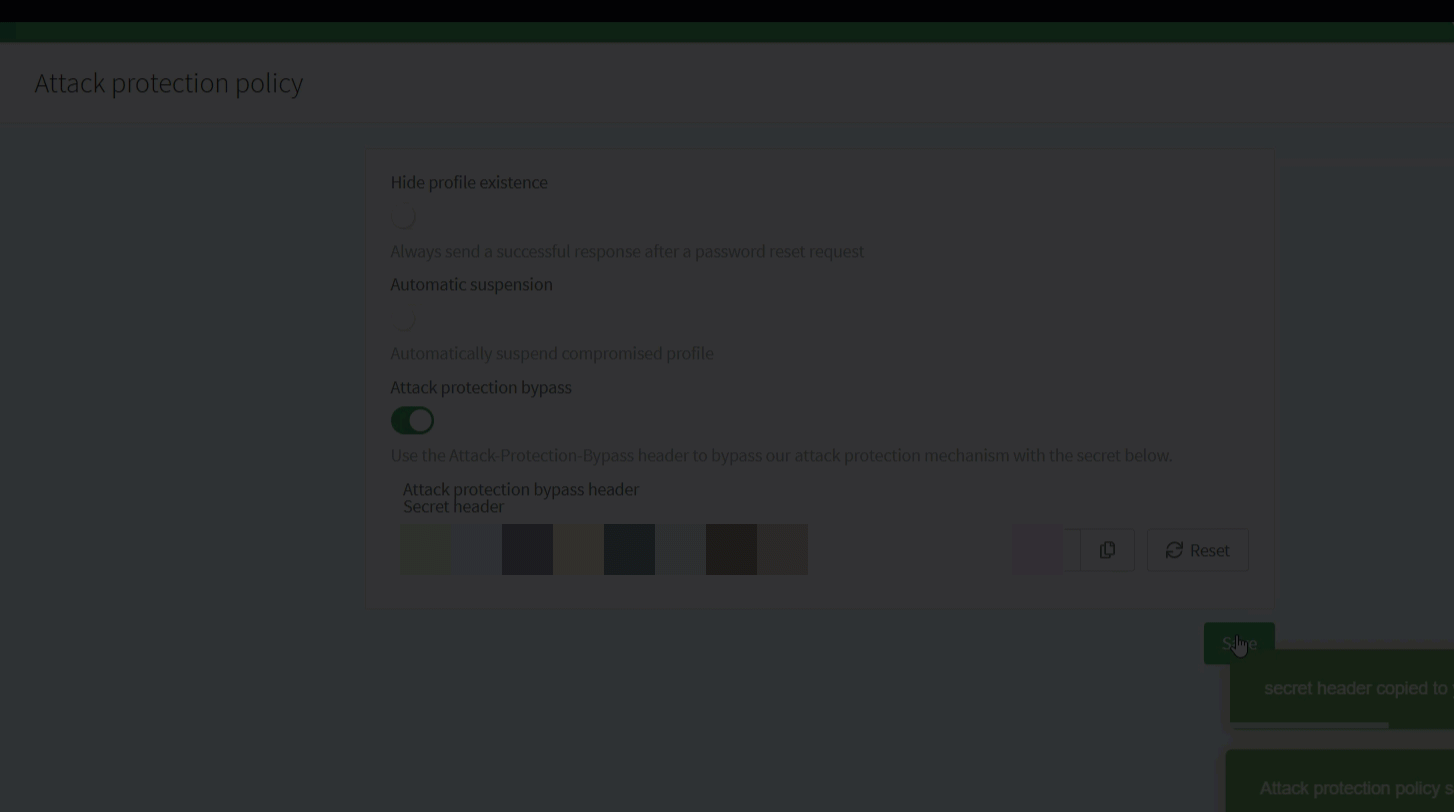
Attack protection bypass header
If you use a pool of IPs that are dynamically updated to call our platform, it can sometimes be difficult to maintain the whitelisted IPs list directly in the ReachFive Console. For this reason, we’ve added the ability to send requests with a secure header. This is called the Attack-Protection-Bypass header and it can only be generated and maintained directly from the ReachFive Console ensuring maximum protection but adding more flexibility for your setup.
The header should only be used from the backend for security purposes.
For more on this topic, check out the Attack protection bypass header section on the Identity Fraud Protection page.
Compromised profile management
It’s now possible to uncompromise[1] a user directly from the ReachFive Console, giving you even more control over managing user profiles.
For more on this topic, check out the Uncompromise a profile section on the Identity Fraud Protection page.
Other improvements
-
Social provider secrets are not viewable from the ReachFive Console. You can update the secret if needed from the console, but it will not be viewable again after saving the information. This is a security-related improvement.
-
You can now filter pre-filled optional fields by
is empty(exists) andis not empty(missing).
Fixes
| Item | Fixed |
|---|---|
In limited circumstances, some scheduled |
✓ |
If several Pub/Sub hooks were triggered by the same event and one of the hooks crashed, the remaining hooks were not called. |
✓ |
Pub/Sub hooks and webhooks were unexpectedly failing when the consent feature was disabled. |
✓ |