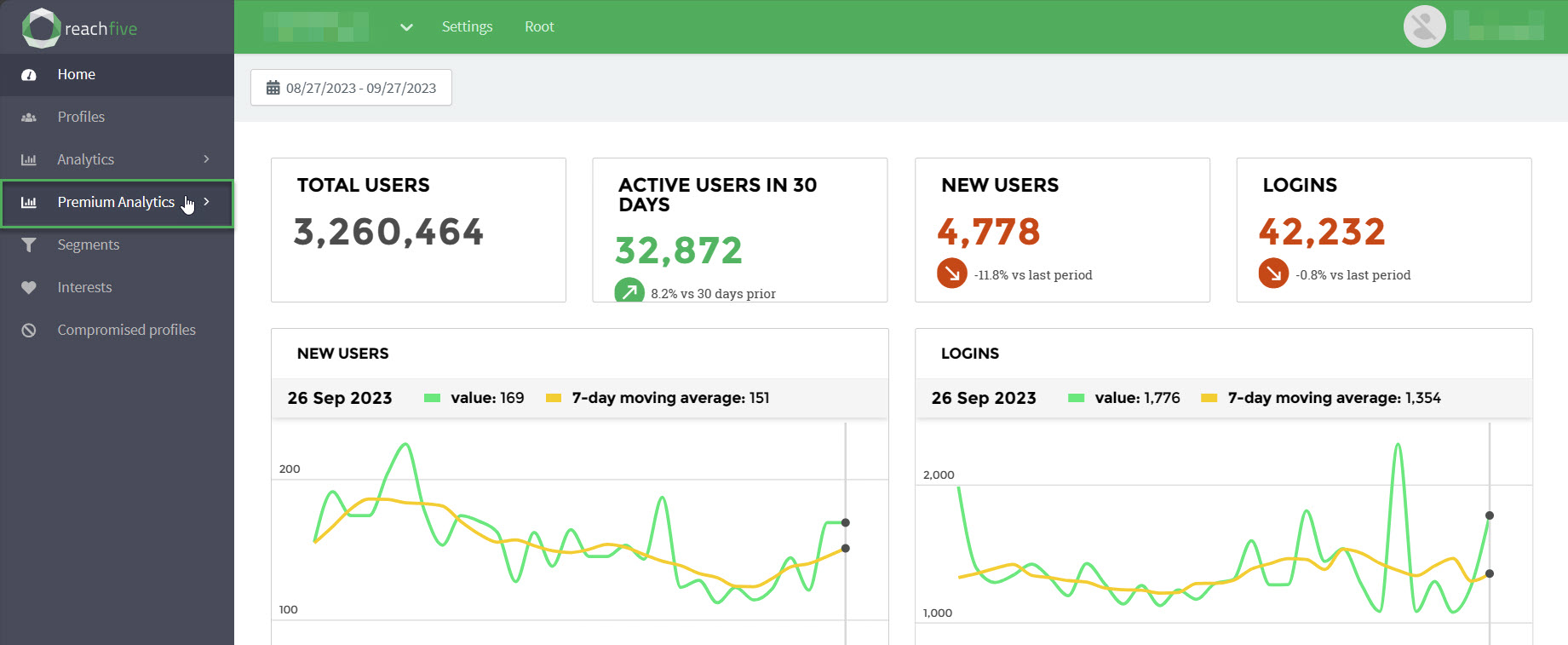
5 October 2023 (v2.101)
ReachFive v2.101 introduces our Premium Analytics, updates the Identity Fraud Protection module, makes some important updates to our WeChat Connector, and brings some other improvements as well. As always, we fixed a few issues.
Identity Fraud Protection
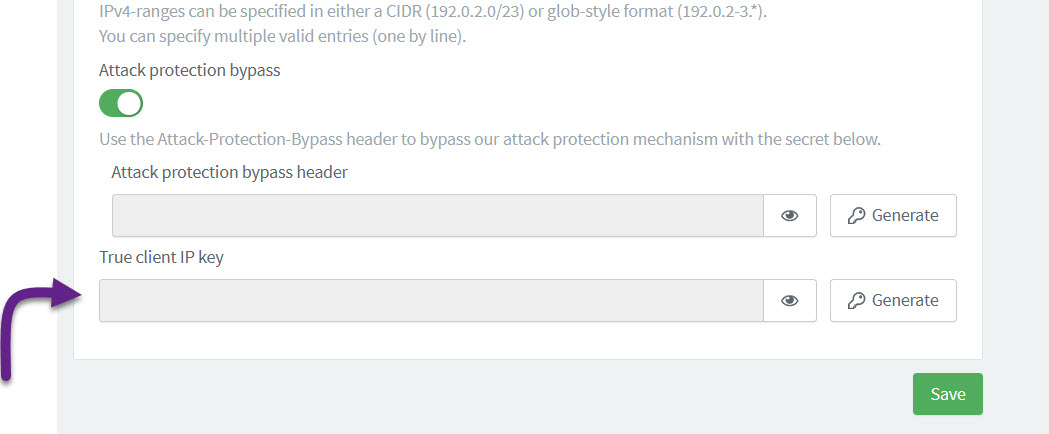
We have made some updates to our Identity Fraud Protection (IFP) module whereby you’re now able to protect requests from the backend, ensuring all customers are able to leverage the powerful IFP functionality. This is done via a new secure header called True-Client-IP that contains the user’s IP.
You can find this on your ReachFive Console at .
For more, see Identity Fraud Protection.
WeChat Connector updates
WeChat is now fully available in our Android SDK. Users are redirected to their WeChat app on Android, allowing you to leverage the full potential of our connector on Android devices.
To ensure optimal functionality with our WeChat Connector, we updated the ReachFive Console so that you can configure your mobile app Client ID and Client Secrets separately.
For more, see WeChat Connect.
For more on Android integration, see our Android SDK docs.
Other improvements
-
We have ensured that expired trusted devices are properly removed from the database.
For more, see Risk-based Authentication.