Stepup required
The following actions require users to go through the stepup flow:
| Operation | Notes | ||
|---|---|---|---|
In order to update an email that is used as a second factor for MFA, users must go through a stepup flow. |
|||
In order to delete an email that is used as a second factor for MFA, users must go through a stepup flow. |
|||
In order to update a phone number that is used as a second factor for MFA, users must go through a stepup flow. |
|||
In order to delete a phone number that is used as a second factor for MFA, users must go through a stepup flow. |
|||
|
If there is already an existing MFA credential, users must go through the stepup flow to add a new MFA credential. |
||
If a user has an existing registered MFA credential and the MFA required setting is set to Always, a stepup is required to login.
|
Using the stepup endpoint
When you use the stepup endpoint to initiate the stepup flow, you can start the flow in one of three ways.
| See the table below for accompanying details to the flowchart. |
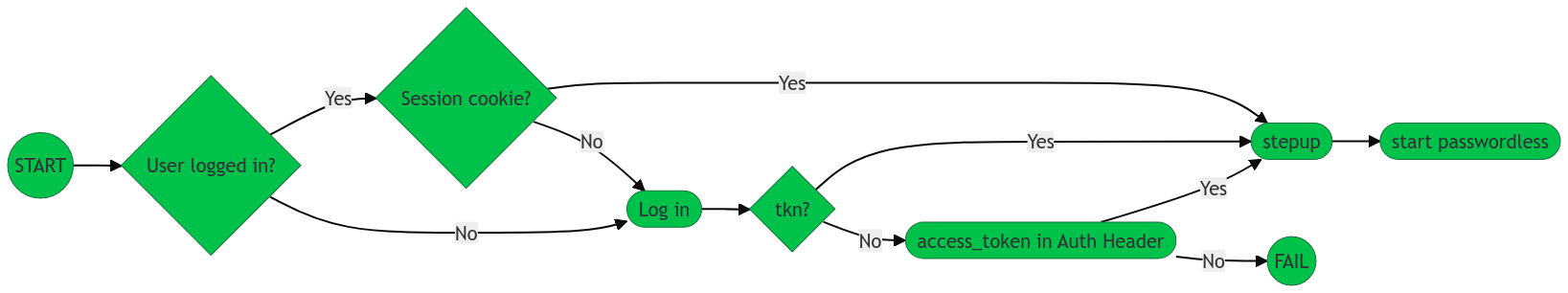
| Approach | Description | ||||
|---|---|---|---|---|---|
SSO session cookie Recommended |
Using a current, active SSO cookie initiates the With the SSO session cookie, the cookie is deposited by the SDK into the browser. This way, it can’t be leaked or used on another domain.
|
||||
Recommended |
Passing a valid |
||||
|
Passing the
|
Retry MFA step-up
In some cases, a user may not receive the MFA verification code (for example, due to SMS or email delivery issues).
To improve the user experience, the step_up token issued during the step-up flow can now be reused to request a new code.
This allows integrators to implement a retry process without forcing users to repeat the full login or step-up flow.
The verification code requests in the MFA flow are subject to a limit. As soon as a new verification code is generated, the previous code becomes invalid. This limit helps protect against abuse and can be configured by ReachFive administrators. If you’d like details on the limit or to adjust this setting, contact your ReachFive representative.
| Step | Action | Notes | ||
|---|---|---|---|---|
1 |
Trigger step-up |
Call |
||
2 |
Start passwordless MFA |
Call |
||
3 |
Code not received? |
If the user doesn’t receive the code, call
|
||
4 |
Verify MFA |
Once the user receives the code, call |
