System for Cross-domain Identity Management (SCIM)
The System for Cross-domain Identity Management, better known as SCIM, is a specification that is specifically designed to simplify managing user identities in cloud-based settings. The primary purpose of SCIM is to automate (in a secure fashion) exchanging user identities between cloud applications and service providers.
SCIM provides a REST API with standard CRUD operations that allows you to do things such as create, update, and delete specific users as well as perform bulk operations, patches, and more.
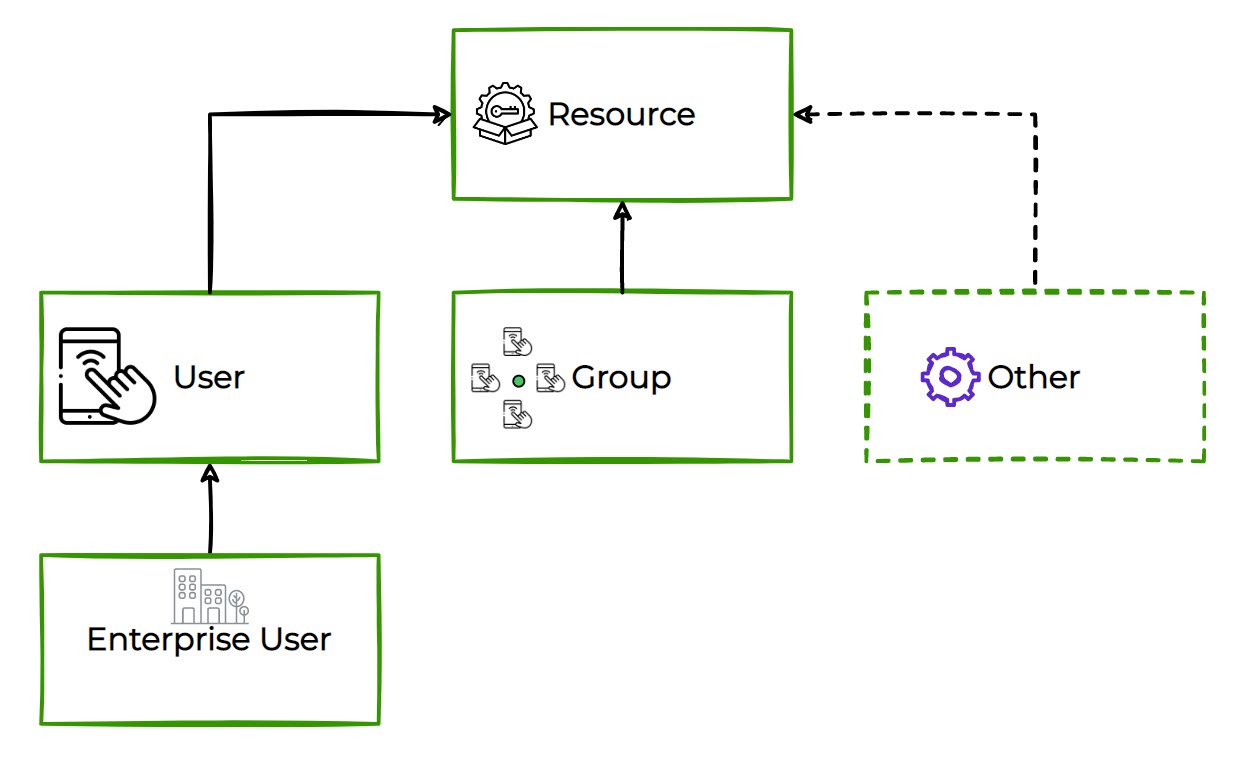
User mappings
User mappings are an integral part of SCIM. With ReachFive’s SCIM offering, you can easily map your brand’s users with roles on the ReachFive Console. This typically means that you can take your user groups, for example admins, developers, read-only users, and so on and forth and map them to ReachFive roles.
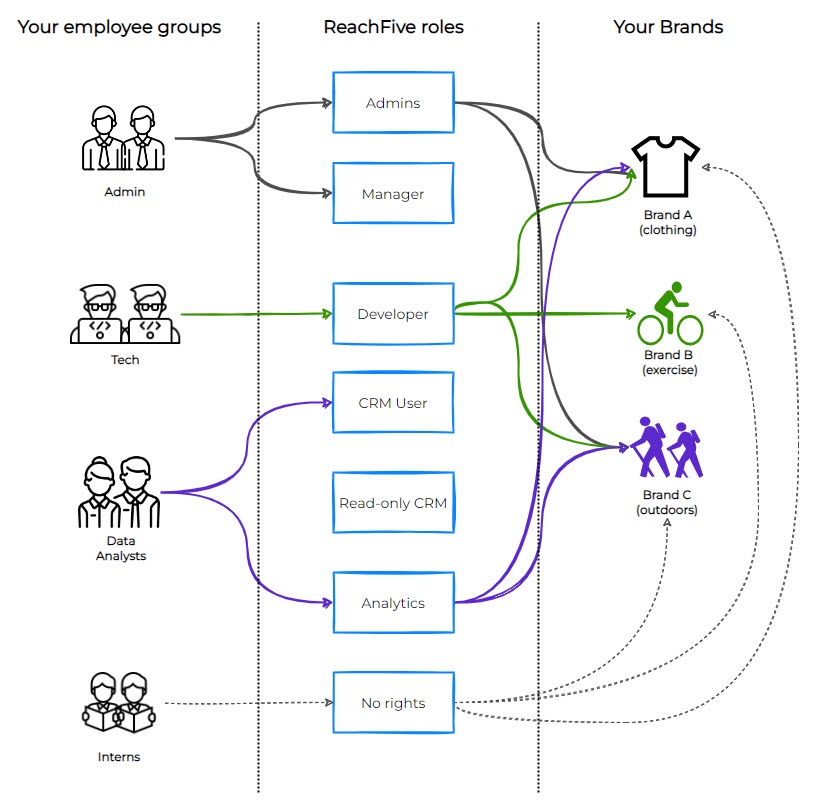
But that’s not all. Through the mapping process, if you have multiple brand accounts, the mappings can be for one or more of your brand accounts for any particular user as they’re mapping from User > Group > R5 > Brand. Check out the visual below to get a better idea of how it works.
| To learn how to create these mappings directly from your ReachFive Console, check out SCIM on the console. |
Console authentication
You may have a situation where you need to ensure that only users who are a part of your oganization can authenticate into the ReachFive Console after you have mapped your groups to ReachFive roles. You can choose to enforce a rule whereby users only are able to authenticate via your user management tool or via the ReachFive Console. You can also enable them to authenticate via either means.
To do this, you’ll need to apply which means is acceptable as part of your user mapping on the ReachFive Console.
For more on setting up and configuing SCIM in the console, see here.
Microsoft Entra ID query considerations
If you are using Microsoft Entra ID (formerly Azure AD) as your identity provider, you must append a specific compatibility flag to your Tenant URL. This only applies to automatic provisioning and not on-demand provisioning.
Entra ID’s default SCIM implementation does not fully comply with the SCIM 2.0 specification regarding group updates. Without this flag, removing a single user from a group in Entra ID may cause the entire group to become empty in ReachFive.
To fix this:
When configuring the Tenant URL in the Microsoft Entra ID portal, add the query parameter ?aadOptscim062020 to the end of your ReachFive SCIM URL.
-
Standard URL:
https://<scim-url>/scim/v2 -
Required URL for Microsoft Entra ID (Azure AD):
https://<scim-url>/scim/v2?aadOptscim062020
| For details, refer to the Microsoft documentation on SCIM compatibility. |