18 July 2024 (v2.116)
ReachFive v2.116 introduces a few improvements and needed bug fixes.
We’re happy to introduce two new user event types.
You can also now retrieve the account_name in a Pub/Sub audit log response.
It’s possible from this release to modify origins through import jobs.
We’ve also updated the ReachFive Console to ensure consent types are not preselected and made some improvements for orchestrated flows.
As always, we made some general improvements and fixed a few items for you.
New user event types
We’ve introduced two new user event types related to passkeys.
-
webauthn_credential_created: Emitted after a passkey was successfully created. -
webauthn_credential_deleted: Emitted after a passkey was successfully deleted.
For more information, see User Events.
The new user event types are searchable with the following endpoints:
You can also use them with Pub/Sub hooks and Post-event webhooks.
Account name in Pub/Sub audit response
In order for administrators to more closely follow and make decisions on how critical or important an event is, we now retrieve the account_name in the Pub/Sub audit log response.
account_name is only present in the Pub/Sub message, not the API response.
|
For more information, see Audit logs.
{
"user_email": "user@gmail.com",
"entity_name": "jobs",
"user_name": "My user name",
"action_name": "create",
"account_name": "top-account", (1)
"created_at" : "2021-09-09T09:21:22.107809Z",
"id": "a040230b-60...998",
"ip_address": "x.x.x.x",
"action_data": {
"jobId": "AXvK4s..UnUYyz",
"jobType": "export"
},
"client_id": "Console ReachFive",
"user_agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/93.0.4577.63 Safari/537.36"
}| 1 | account_name specifies the name of the ReachFive account. |
Modify origins with import job
You can now modify the origins user profile field through import jobs.
This is valuable in recovery situations, error resolution, or integration issues.
| The import job overwrites any existing origin(s). |
What is an origin? 🤔
An origin is the channel through which the user authenticated.
This could be a website, or perhaps a mobile app.
It is defined via user interaction and only authenticated profiles contain origins.
This means lite profiles do not contain the field.
You can value this field via the Identity API, our SDKs, and through imports. However, the field cannot be valued through the Management API.
...
"origins": [
"web",
"xbox"
],
...For more information, see User Profile.
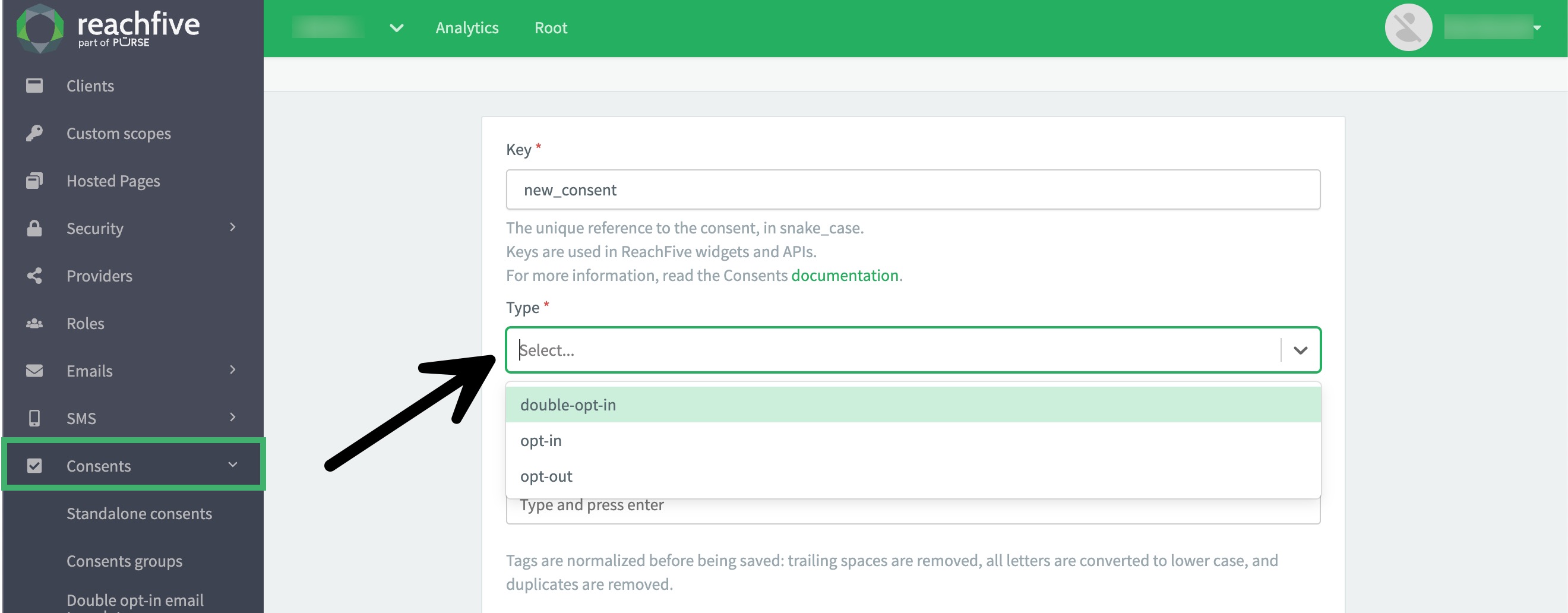
No preselected consent type
We now ensure there is no consent type preselected when creating a new consent in the ReachFive Console. This ensures all consent types are intentionally chosen by the person creating the consent.
For more information, see Consents.
Improved orchestrated flows
We now handle prompt=none in a standard fashion to better support orchestrated flows, meaning that the flow can now properly perform silent authentication.
This was made possible through a much needed fix described below.
| Silent authentication mandates no user interaction, which is why we redirect back with an error if no session exists. |
Other improvements
-
We’ve improved the wording under the recent activity section of the ReachFive Console for when users log in with a custom identifier.
New wording: Logged-in using password with custom_identifier
-
You can now connect to the ReachFive Console with Okta.
-
We’ve made some changes to ensure better stability for import jobs.
-
For those using Oracle Responsys, we now include a
booleanto check if a user’s email is verified so you can better customise your email templates.
Fixes
| Item | Fixed |
|---|---|
There was an issue with editing consents if changes were made (such as archiving a consent) in the ReachFive Console. This was affecting consent validation, but it has now been fixed. |
✓ |
In some cases, even when toggled off, some social providers continued to be shown as available in the ReachFive Console. This was causing some providers to inadvertently appear in UI widgets and hosted pages. |
✓ |
It was temporarily impossible to add URLs with hyphens ( |
✓ |
We now ensure all MFA activations are shown properly in our Premium Analytics . |
✓ |
✓ |