21 November 2024 (v2.124)
ReachFive v2.124 introduces a few improvements and needed bug fixes.
You can now specify which identifiers are allowed to attempt to log in to your site.
We made some important Risk-based authentication updates.
You can also now pass the variant name for social providers directly through the iOS SDK.
For the UI SDK, we have added the allowPhoneNumberResetPassword parameter so users can use a phone number to initiate the password reset flow.
In addition to the above, you can now update a user password hashing algorithm with the Management API.
As always, we fixed a few items for you.
Allowed identifiers
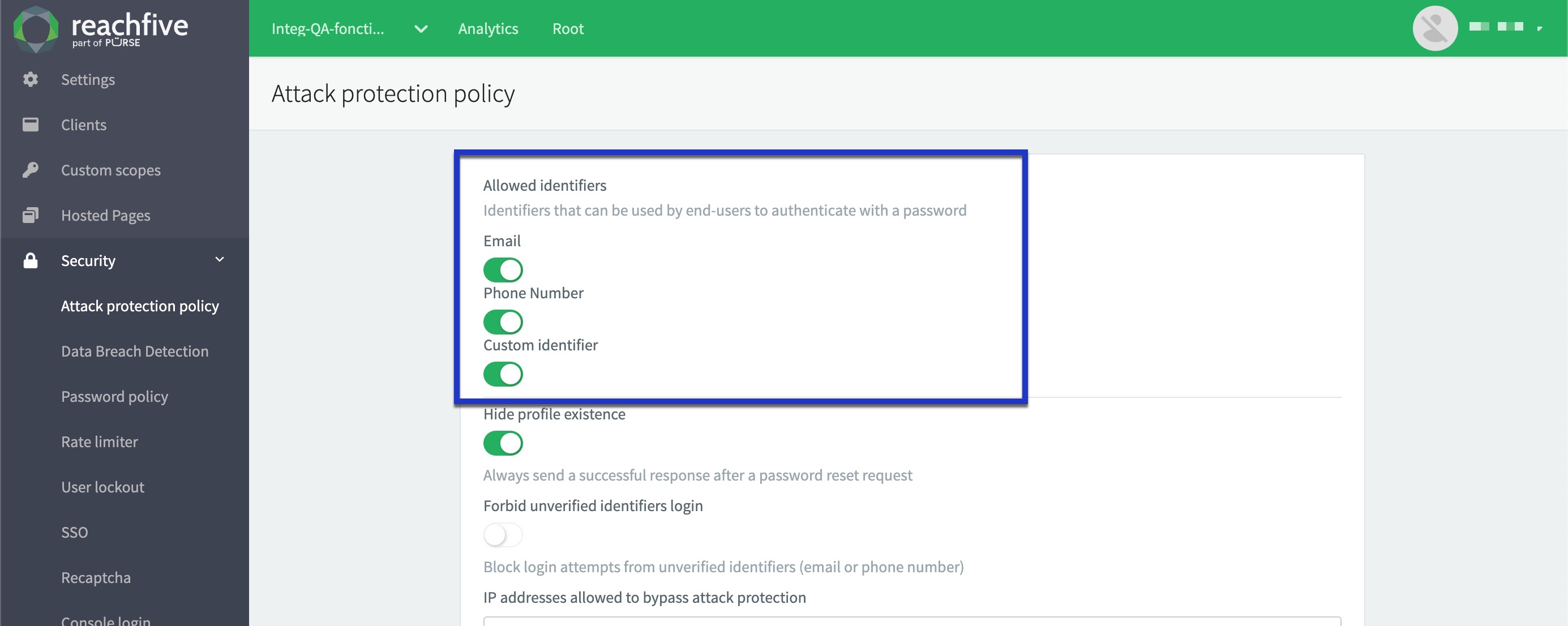
You can now specify which identifiers are allowed to attempt to log in to your site. The feature provides an added layer of control to ensure that only matching identifiers are allowed to log in, streamlining the authentication process and enhancing security for your setup. This configuration only applies to password authentication. The configuration does not affect social logins, passwordless, or passkeys.
For more details, see Specify allowed identifiers.
Enable this in the ReachFive Console:
-
Go to .
-
Toggle which identifiers you want to be able to attempt to log in to your site. Those that are not enabled will no longer be able to attempt logins.
-
Email
-
Phone Number
-
Custom identifier
-
-
Don’t forget to Save your input..
Error message
Users that attempt to login with an unverified identifier receive an error message informing them that they cannot log in with the specified identifier.
You cannot authenticate using {0}
- Affected endpoints
Risk-based authentication updates
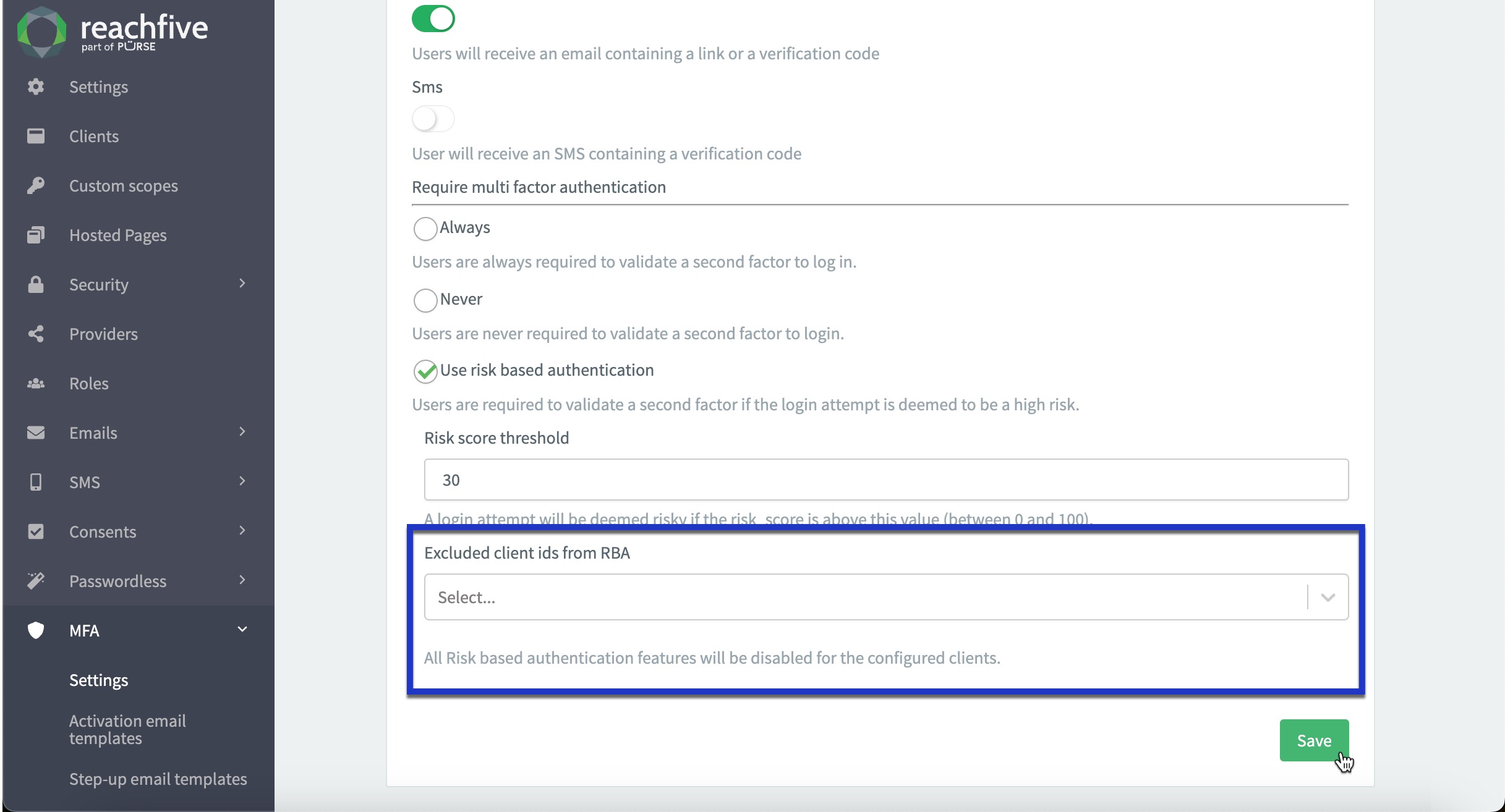
We’ve enhanced our Risk-based authentication (RBA) feature to give you greater flexibility and control. You can now exclude specific client IDs from RBA protections directly through the ReachFive Console, ensuring tailored security configurations that suit your unique needs.
For more, see Risk-based Authentication.
Define provider variant
We’re happy to introduce a new capability in our iOS SDK for social providers like Apple, Facebook, Google, and WeChat. You can now pass a specific "variant" name directly through the provider object to tailor the behavior for your use case. If no variant is specified, the SDK uses the first variant with "ios" in the name.
static let reachfive: ReachFive = ReachFive(
sdkConfig: sdkRemote,
providersCreators: [
GoogleProvider(), (1)
FacebookProvider(variant: "ios_app"), (2)
AppleProvider(variant: "ios_default"),
WeChat(variant: "ios17")]
)| 1 | Here, no variant is passed so the object takes the first variant containing ios in its name. |
| 2 | Example of defining an ios variant. |
This feature provides added flexibility for scenarios like:
-
Multi-brand Apps: Seamlessly support distinct branding or custom login flows for different app versions by specifying the appropriate variant.
-
Testing and Debugging: Quickly switch between variants for A/B testing or troubleshooting without altering server-side configurations.
For more details, see iOS SDK.
Update user password with Management API
You can now update a user password hashing algorithm through the Management API.
To do this, you should use the /users/:userId endpoint and pass the following as part of the request body:
{
...
"password_hash": {
"value": "$2b$12$KIXwPlj7FZ9dTjph4GxGhu3ofk1KFe.KjLw6gNlD72zyGIBlIL7H6", (1)
"algorithm": "plaintext" (2)
}
...
}| 1 | Pass the hashed password. |
| 2 | Specify the encryption algorithm, such as bcrypt.
See Allowed algorithms for more details. |
Fixes
| Item | Fixed |
|---|---|
There were some inconsistencies on custom fields with the data type |
✓ |
Some user login data returned from a webhook was not taken into account on the user profile. |
✓ |
There were some minor UX issues for Analytics on the ReachFive Console. |
✓ |
For a brief period, changes to SMS templates were not being saved on the ReachFive Console. |
✓ |
You were temporarily unable to save updates to the Adobe Campaign email template. |
✓ |