01 July 2024 (v2.115)
ReachFive v2.115 introduces a few improvements and needed bug fixes.
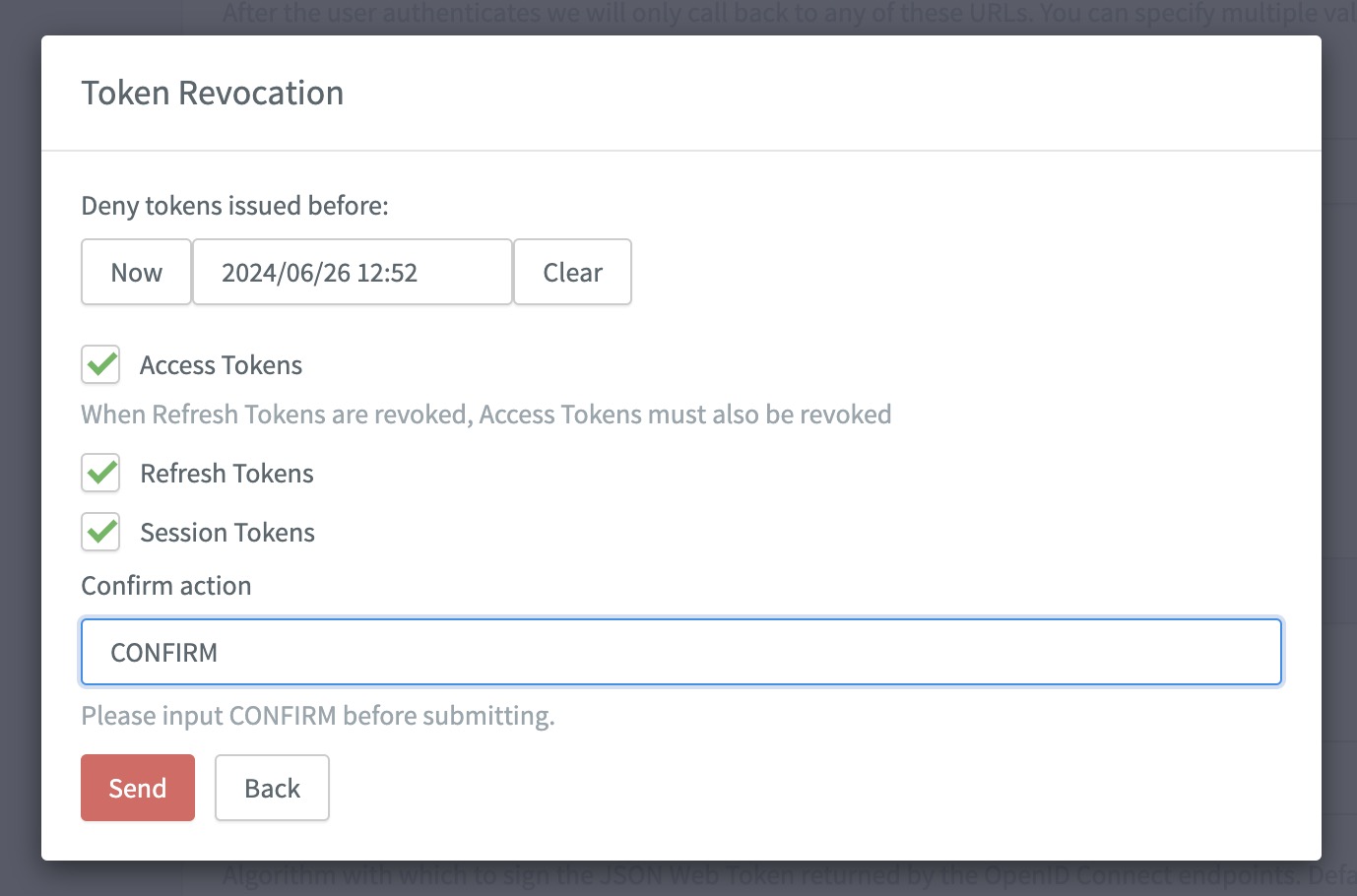
With this release, you can now revoke user tokens at the client level.
The transports claim is now fully available in the public key response for the /webauthn/authentication-options endpoint.
You can also now perform the stepup operation in more ways including using social provider logins for MFA second factors.
As always, we made some general improvements and fixed a few items for you.
Revoke tokens at the client level
You can now revoke user tokens at the client level directly from the ReachFive Console. This is applicable to both First-party and Third-party Identity clients, but not Management clients.
For more information, see Clients.
transports in WebAuthn endpoint response
The transports claim is now fully available in the public key response in the allow_credentials object.
Affected endpoints:
The transports field assists the Relying Party (the service requesting authentication) in understanding how the authenticator can be communicated with.
| This is useful for optimizing both user experience and troubleshooting any potential authentication issues. |
{
"public_key":
{
"allow_credentials":
[
{
"id": "X9FrwMfmzj...",
"type": "public-key",
"transports": ["ble", "internal"] (1)
}
],
"challenge": "kYhXBWX0HO5GstIS02yPJVhiZ0jZLH7PpC4tzJI-ZcA=",
"rp_id": "demo.reachfive.com",
"timeout": 120000,
"user_verification": "discouraged",
},
}| 1 | List of transport types supported by the authenticator.
For more details, see WebAuthn transports. |
Perform stepup with other authentication methods
Previously, for users to perform a stepup operation, they needed to have initially logged in with a username and password combination.
Now, they can authenticate with their chosen method, including Social Login providers such as Google, Apple, Facebook, or any other supported social provider and still partake in the stepup flow.
In the social login case, amr is valued with the authentication method slo.
For more details, see Multi-factor Authentication.
Other improvements
-
We now ensure that any invalid provider type is ignored during user imports, ensuring a smoother, more reliable import process.
-
We improved the error messaging for when users attempt to use MFA on a lite profile. Now, you’ll receive the
error.mfa.noLiteOnlywith the message that "A lite profile cannot register a mfa credential".Affected endpoints include
mfa/credentials/phone-numbersand/mfa/credentials/emails -
You can now manage your employees that authenticate via Okta using our SCIM feature.
For more information, see SCIM.
Fixes
| Item | Fixed |
|---|---|
In some cases, there was a discrepancy between the expiry of the challenge and the verification code. |
✓ |
In some limited circumstances, the User Event ID wasn’t being exported as part of export jobs. |
✓ |
When confirming a Double opt-in consent, users were unexpectedly receiving an invalid token error. |
✓ |